Encrypted storage entropy tests
Today I've got my new 128G USB flash drive from Hong Kong, intending to use it as an additional encrypted storage. Setting up LUKS volume implies filling all the drive with random data first, to avoid possible statistical attack. I've plugged USB in, created random data key file, formatted the stick as LUKS volume, and started feeding it with /dev/zero contents via dd, using LUKS infra as an entropy source (it's faster than dd'ing /dev/urandom). But 128G is kind'a lot for an usb drive, so, even using this trick it took several hours. I was wondering if it's really that necessary, so, decided to do some syntheric tests.
There are plenty of tools for binary data and entropy visualisation out there, I was using the first google hit for that.
case 1:
Empty file, filled with zeros, resembling "factory format".
$ dd if=/dev/zero of=test.img bs=1M count=6
result: entropy-test1.png
case 2:
Adding LUKS header.
$ sudo cryptsetup luksFormat -q -v -d /tmp/keyfile test.img
result: entropy-test2.png
case 3:
Creating filesystem within encrypted container.
$ sudo cryptsetup luksOpen -d /tmp/keyfile test.img test_crypt
$ sudo mkfs.ext4 /dev/mapper/test_crypt
$ sudo cryptsetup luksClose test_crypt
result: entropy-test3.png
case 4:
Filling HALF of the container size with zeros via LUKS, creating FS on top.
$ sudo cryptsetup luksOpen -d /tmp/keyfile test.img test_crypt
$ sudo dd if=/dev/zero of=/dev/mapper/test_crypt bs=1M count=3
$ sudo mkfs.ext4 /dev/mapper/test_crypt
$ sudo cryptsetup luksClose test_crypt
result: entropy-test4.png
case 5 (the right way):
Formatting LUKS, filling ALL the storage vis zeros via LUKS,
killing LUKS header space via /dev/urandom, rebuilding LUKS,
creating FS on top.
$ dd if=/dev/zero of=test.img bs=1M count=6
$ sudo losetup /dev/loop0 test.img
$ sudo cryptsetup luksFormat -q -v -d /tmp/keyfile /dev/loop0
$ sudo cryptsetup luksOpen -d /tmp/keyfile /dev/loop0 test_crypt
$ sudo dd if=/dev/zero of=/dev/mapper/test_crypt
$ sudo cryptsetup luksClose test_crypt
$ sudo dd if=/dev/urandom of=/dev/loop0 bs=512 count=4096
$ sudo losetup -d /dev/loop0
$ sudo cryptsetup luksFormat -q -v -d /tmp/keyfile test.img
$ sudo cryptsetup luksOpen -d /tmp/keyfile test.img test_crypt
$ sudo mkfs.ext4 /dev/mapper/test_crypt
$ sudo cryptsetup luksClose test_crypt
result: entropy-test5.png
Compare:
entropy-test1.png |
entropy-test2.png |
entropy-test3.png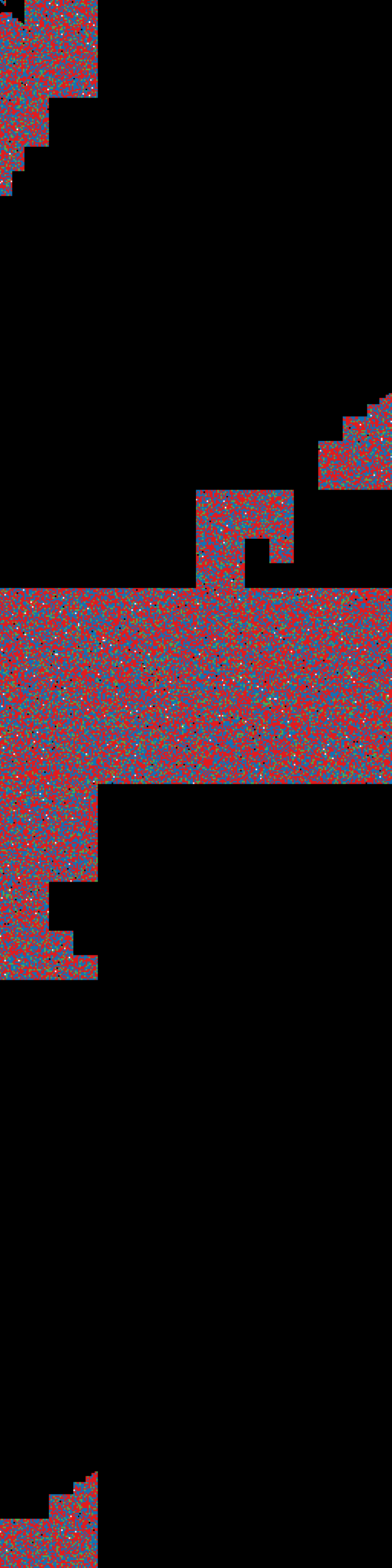 |
entropy-test4.png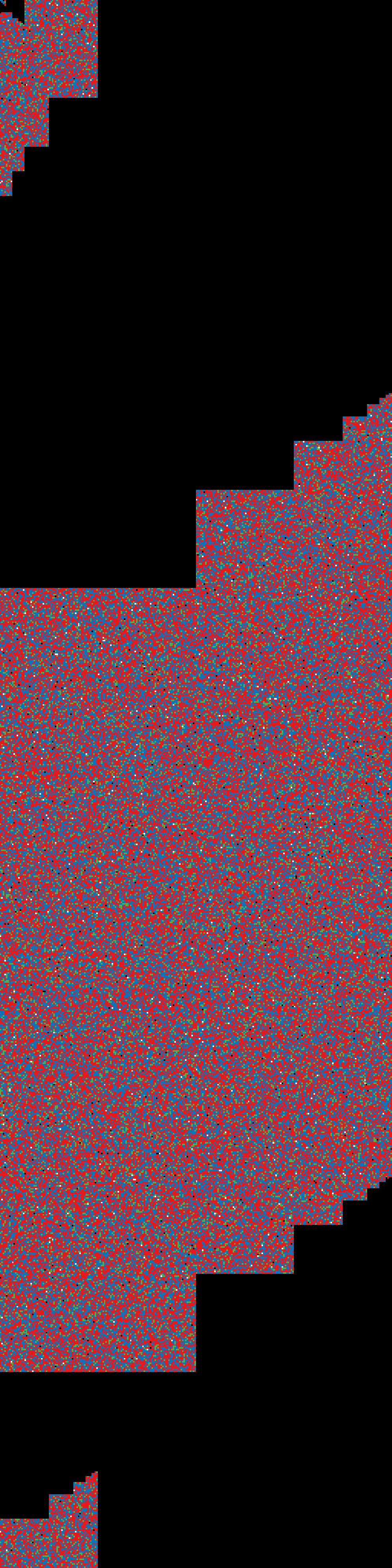 |
entropy-test5.png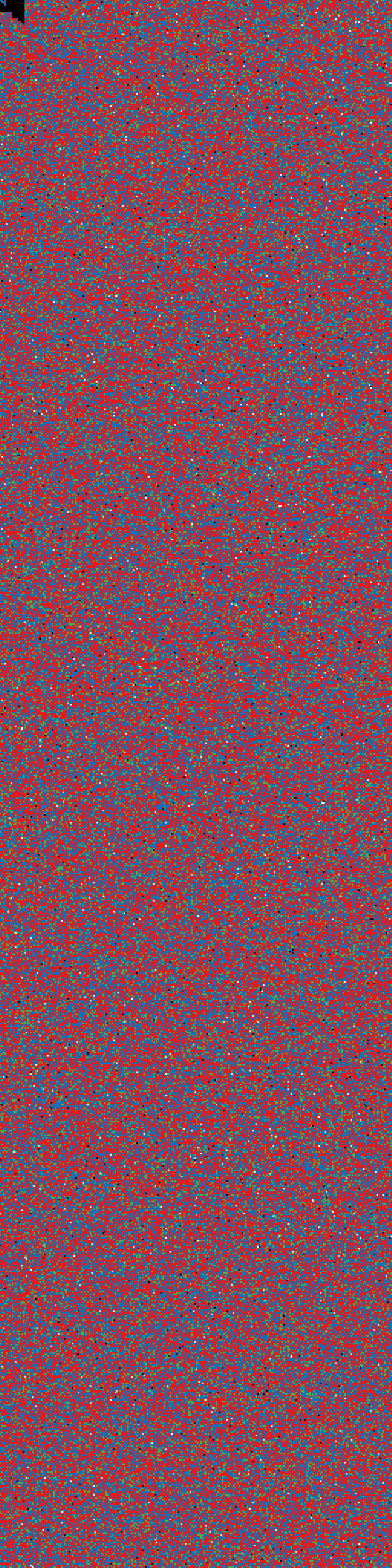 |